Cybersecurity expert Denis Boudy joins Caroline Zigrand, New Business Developer at Wave by AGC, and the WAVETRAP team to discuss why businesses across the EU need to consider how vulnerable their workspaces are to hackers in regard to the NIS2 regulation. And more importantly, why they should contemplate all the different ways to protect them.
Caroline – What was the tipping point that lifted cybersecurity awareness out of the shadows and made it a mainstream concern?
Denis – It wasn’t one single event that turned the tide on this topic, but rather several key factors that brought the topic of cybersecurity into the spotlight. Over the last years, there’s no denying the steep increase of cyber-attacks in various markets worldwide, the relentless small-scale phishing scams in our personal lives and the large-scale ransomware threats in our professional lives. The desire and need for a solution that provides a secure collaboration, where data could be handled, stored, or even manipulated in a safe environment, has never been greater.
The ratification of the NIS2 Directive in November 2022 – something France pushed hard for to address growing concerns over the evolution of cyber threats – has also proved to be a catalyst in this process, with a planned implementation for 2024 across the European Union.
Collectively, this represents the ‘tipping point’ where member states and the organisations within them began to see both the moral obligation (accountability) to address these concerns and the legal obligation to prepare and apply the appropriate security measures throughout the supply chain.
Everyone is a potential target. It concerns us all.
Caroline – Does protecting digital assets include also protecting everything which generates data, such as the devices and the buildings they are located in?
Denis – Indeed, it really does concern every kind of device or piece of connected hardware within a building that generates or processes digital assets. It covers everything relating to an information system, ranging from buildings and production lines to stationary and mobile devices.
The building itself and its infrastructure already offer a serious security perimeter – from CCTV systems to IoT (Internet of Things) devices connected to the network, there are so many different points across the network that process or store sensitive data.
For me, there are three key levels of information:
- The main IT system – This extends to my desktop working space (laptop, mobile device, etc) that I used to work on a day-to-day basis, accessing company data.
- Building operating system – Smart buildings offer an amazing way to empower staff and create more energy-efficient works spaces, with IoT devices across its infrastructure feeding into a centralised management and operation system.
- Production operating system – This extends to everything linked to a production line, including power supplies and production information linked to a network.
All three levels of information here must communicate with one another so organisations can gain a realistic insight on the real-world global stakes facing the cybersecurity community. If this type of communication and transparency isn’t forthcoming, then the threat of cyber-attacks will only grow.
This is why we must all consider a building’s digital permeability. If we do not, we open ourselves up to attack.
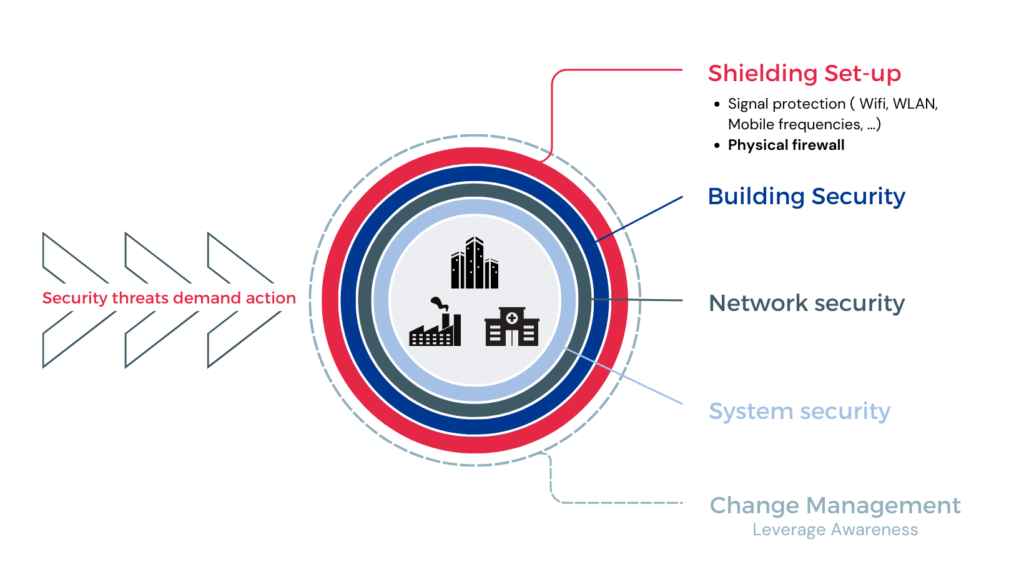
Caroline – What would be your top recommendations on how organisations can increase their cybersecurity protection?
Denis – Beyond the NIS2 regulation, there is a plethora of precautions and proactive actions you can take to address these issues from both a digital perspective and a physical one.
Whether you’re looking at this from a virtual or physical perspective, there are some key recommendations you should always consider:
- Stakeholder responsibility – Ensure that everybody knows that every member of the team has a role to play and a responsibility when it comes to upholding cybersecurity best practices.
- Establish the right systems – To ensure these policies are followed, you must establish a workflow of recurrent risk analysis and resilience systems.
- Sensibilise all stakeholders – Ensure that all teams, at all levels throughout the organisation are educated to better understand the importance of responsible cybersecurity online.
- Familiarise the technology – Your digital policies and procedures are powered by the right technology, so ensure all members of the organisation are on side.
For example, on a dedicated project, we found a BIM (Building Information Modelling) convention that contained a directory of sensitive stakeholder information including:
- Name
- Address
- Phone number
- Company
- Location of the building
- Planning information
- CCTV information
- Power and energy details
- Cloud information
- The digital platform in use
All this information was and remains highly attractive to hackers. This binding document could be the perfect treasure trove of information as it already details who works on which project when and where. This is the type of information you do not want to fall into the hands of hackers. Limited protection might lead to maximum exposure with extreme reputational, financial, and judicial repercussions.
Even from a physical perspective, we can take the same example. For instance, we might decide to print the above BIM convention then take a copy with us to an in-person meeting to share it with project stakeholders. However, if I forget to take it with me or let it linger somewhere on the table, then there’s a huge physical data breach. It may have been left behind by accident, but you can no longer afford to take that risk.
Sometimes you see people typing away on the train without shielding the contents of their laptop screen. They might be working on their grocery list, or on their defence in a high-end lawsuit. Just imagine you maliciously take pictures of the latter and sell this valuable information to the other lawyer. You’ve lost an entire case because of your own carelessness.
That’s what I meant earlier with everyone being a target. Data is the new currency, and information can secure hard cash. The hacking equipment is getting smarter and cheaper by the day. And so is the business approach of some hackers, I have even seen cases where they offer a gold/premium/freemium business model – where you are taxed on response time.
We must be always aware and accountable.
Caroline – What about NIS2?
Denis – NIS2 is a much broader directive than its predecessor, extending its legislation to a larger number of companies (such as SMES with 250 employees and sales starting at 10 million euros) and there are now steeper penalties for non-compliance (including fines of up to 10 million euros or the equivalent of 2% of its turnover).
There are 23 business sectors now affected, covering both essential and other important businesses. Behind them, the supply chain itself is likely to host subcontractors with their own responsibilities (such as in France, where changes to military programming law in 2024 will have a considerable ripple effect).
IT managers are going to have to re-evaluate how they process, store, and manage sensitive data both physically and digitally and how these policies are developed and followed. There are still plenty of grey areas not covered by this new directive, so there is plenty of work still to be done.
Caroline – Can smart buildings meet the challenges of NIS2?
Denis – Yes, but indirectly. We need to make as many people as possible aware of the challenges of cybersecurity. Not only the terms of the NIS2 regulation.
If we build an intelligent building, information will circulate so we need to set up automated tools to help with navigation and IoT connectivity, but if cybersecurity isn’t a core consideration for the network, these devices could present a devastating means of access for hackers to exploit.
In 2022, the Smart Building Alliance in France published a white paper that discussed cyber risk at the building level and the challenge NIS2 presents for companies when it comes to making their smart buildings fully compliant.
Caroline – How can glass impact the protection effort against cyber-attacks?
Denis – There are many ways glass as a material can be used to protect smart buildings from external cyberattacks. A good example is La Poste in France, which developed a data backup storage unit for SMEs that utilised a glass wall for adding an additional layer of protection against electromagnetic waves.
Cybersecurity is a lot like an onion – the harsher the winter, the more layers are required! The same concept applies to cybersecurity. The more layers of protection we apply to a building or a server room, the more resilient it is to attacks.
Specialised glass solutions are just one of the ways we can proactively protect our businesses (and our homes) against hackers.
Caroline – How can we best support our customers with this global cybersecurity issue?
Denis – There are three core tenets you need to take into consideration:
- We need to raise awareness among our teams.
- We need to develop strategies.
- We need to involve central management and everyone responsible for information.
We should look at the process as a series of levels of responsibility, accountability, and proactive action regarding cybersecurity in a smart building:
- First level – To maintain a regular watch on risk as individuals, remaining vigilant for us and our customers.
- Second level – Applying cybersecurity policies to the design of projects, whether industrial, infrastructure, etc.
- Third level – Providing and developing turnkey solutions that automate, facilitate, and simplify day-to-day cybersecurity.
Caroline – What advice would you give in terms of cybersecurity for non-experts and experts, especially in regard to the NIS2 regulation?
Denis – It’s up to all of us to play our part in cybersecurity. We need to involve everyone, not just IT, but all stakeholders from every department. It’s a team effort and it requires everyone to commit the process and share their insights. It is a long-term investment, supported by the NIS2 regulation.
A great piece of advice is to ask questions surrounding the lifecycle of any data in your organisation. What information is being processed? Which platforms are being used? Which countries is that data being accessed in? What risks of data leakage are there?
We have an interesting case in France where a region is launching a vast energy renovation program for the secondary schools. There is no data available on the schools, so all this information needs to be collated and gathered. Not a problem with the high-performance tools in the market. Not a problem to collate this vast wealth of school information in a digital model. We issued an invitation to tender to which private companies and surveyors are responding. The thing is, we’re not only looking at their offer and pricing, we are also investigating how and where they are using and disseminating this information. We don’t want to risk malicious minds using these plans to meticulously plan a school attack.
On that note, the risks of physical attacks are just as real as digital ones. It could be as simple as stealing or tapping into a simple piece of equipment left unattended. One moment of carelessness is all it takes.
Ultimately, the most important thing is to question the criticality of the data being processed, beyond tacit and unchecked trust.
Knowing is caring, caring is securing. Know how to always be secure.
Caroline – Where do you find your inspiration? Which sites, books, or podcasts would you recommend?
Denis – I try to keep my eyes, ears, and mind open at all times, but I have these sites bookmarked:
https://www.welcometothejungle.com/fr/companies/anssi
https://secnumacademie.gouv.fr/
https://www.youtube.com/c/CyberVox/videos
https://www.holiseum.com/cybervox-by-holiseum
About Denis Boudy :

Denis has been with Ingerop since 2019 and works on the SreedIn project, aimed to integrate an incubation program with a project linked to the cybersecurity of the engineering data. Professionals can get certified in this field by following an ANSSI (Agence Nationale de Sécurité des Systèmes d’informations) training.
This project is evolving into a commercial brand known as ScredIn. It encompasses the creation of an application and a service package aimed at providing guidance and training related to the application’s usage. Additionally, it aims to raise awareness about cybersecurity risks and NIS2 compliance within the engineering, construction, and industrial sectors.
Contact us for more information

