Cyberattacks are on the rise. Ransomware and malware are an ever-present threat. Phishing scams continue to grow more sophisticated and invasive. In a society that’s become so heavily reliant on the virtual world, the pressure on the cybersecurity community to evolve and respond continues to mount. To instill more awareness on the impact of cybersecurity threats on today’s society, the European Parliament launched the NIS directive, urging companies of all sizes across different markets to improve how their data is collected, collated, deployed, and secured.
In this blog, we’ll be discussing why this new piece of legislation is so important, how it will have wide reaching effects on the cybersecurity community and how professionals can take steps to improve the integrity of their data while ensuring full NIS2 compliance.

What is the NIS2 Directive?
The NIS2 Directive, a piece of legislation from the European Parliament, aims to address this issue by raising the threshold of compliance and refreshing the protections required to mitigate these seemingly unending cyber threats.
Back in 2016, the European Union passed the Network and Information Security (NIS) Directive, a new piece of lawmaking designed to address the security requirements for companies and organisations operating within the critical infrastructure of its member states. While it purely focused on the digital security integrity of ‘essential’ sectors such as aviation, telecoms, and energy, it established a core framework that addresses the importance of strengthening connectivity and the storage of sensitive data.
On the 28th of November 2022, the EU ratified the next stage of its plan to combat growing cybersecurity concerns with NIS2. With a timeline of two years for its member states to bring themselves into compliance, the race is on to introduce new technologies and innovations that not only meet the standards of this law but help establish confidence in the collective cybersecurity. NIS2 is less of a legislative replacement, and more of a progression, extending this framework to a much wider group of organisations that need to deal with the threat of data breaches.
Who needs to follow the NIS2 Directive?
The NIS2 directive is mainly aimed at both:
• essential entities in numerous sectors, such as companies generally accounting for 250 employees, an annual turnover of € 50 million or a balance sheet of € 43 million
• important entities in numerous sectors, such as companies generally accounting for 50 employees, an annual turnover of € 10 million or a balance sheet of € 10 million
Why should everyone be looking at being NIS2-compliant?
Consumer data itself is new bitcoin, and the value of that data continues to drive the frequency and sophistication of these seemingly unending digital attacks on both a small and larger scale. And scammers and hackers will use any technology, physical or digital, at any scale to get ahold of that data. What sort of attacks can we expect?
1. Big scale hacking – the use of Intentional Electromagnetic Interference (IEMI)
Watch any film or TV show involving a heist or a hacking attempt, and there’s a good chance some form of electromagnetic device will be used to disrupt some form of electrical security device. Like most fiction, these devices are inspired by real live hardware, and the reality is much scarier. These devices are used for Intentional Electromagnetic Interference (IEMI) attacks, where an external source is used to halt, hamper, and affect the flow of binary data within the circuits of a physical device.
Since all circuits give off a natural electromagnetic field, practically every form of circuitry is susceptible to this kind of attack. From the smallest devices to hardware that forms part of critical national infrastructure, the potential for these far from fictional electromagnets is truly terrifying. Don’t believe us? Just rewatch Ocean’s Eleven and Goldeneye in the James Bond series.
2. Small(er) scale hacking – employee networking hacking
One of the easiest and most exploited ways to access sensitive company (and personal) data is through your employees. It’s estimated that the majority of cyberattacks rely on some form of social engineering, whereby human error is exploited to reach sensitive data and information. New employees are at a far higher risk of being targeted in this way, so implementing much swifter training and IT awareness procedures is vital.
Phishing attacks have never really gone away, and these scams continue to grow more and more convincing in their resemblance to real emails and messages. Ransomware attacks are also a prevalent threat to your employees and the integrity of your business data, so there’s always some form of threat lurking in the digital shadows.
The NIS2 directive provides a clear outline on the cybersecurity precautions you should be taking to mitigate and minimise these threats, but what about from a physical point of view? Developing, testing, and implementing effective cybersecurity strategies is a complex task that takes plenty of investment of time. And let’s not forget, it takes hackers far less time to crack a measure or protocol than it does to create it in the first place.
So, how should professionals prepare for NIS2?
Preparing your cybersecurity protocols to comply with NIS2 requires both a physical and virtual approach. These preparations can be far reaching depending on the extent of your business operations, and with everything from server capabilities and disaster recovery planning to evaluating cryptography and encryption integrity, there are lots of factors to consider.
Here are a few simple suggestions for your IT department to consider when it comes to portable devices:
• Make sure they are fully secured to negate the impact of hacking attempts.
• Adding layers of additional security makes these defenses even more robust.
• Brief employees to always log out from workstations in the workplace and lock them to ensure no one can simply plug in a USB and start downloading any locally stored data or even connect directly to the network.
• Even printers can store data locally, so securing this kind of hardware is just as important.
The key is to protect what matters – your data, and the connectivity that proliferates it across your network. That’s why C-level conversations are needed to ensure compliance is followed across an entire organisation so that data protection laws are fully addressed. It’s about warding off any form of electronic eavesdropping, while helping to prevent any potential human errors that compromise the integrity of your data.
That calls for more cybersecurity professionals who can help create and implement these cybersecurity strategies. But with the ongoing “cyber poverty” crisis, not all companies will have the luxury to find and hire dedicated professionals to look into the matter. In which case, it is better to broaden the company scope and explore physical measures that will help prevent human and virtual vulnerabilities.
Mind you, The European Commission set the goal of reaching 80% of adult EU citizens with basic digital skills and 20 million employed Information and communications technology (ICT) specialists by 2030. That is why they launched a Cybersecurity Skills Academy on April 18th, 2023 to close the cybersecurity sector’s ongoing skills shortage and develop the EU’s cyber resilience.
What kind of physical measures can you implement?
The whole is always greater than the sum of its parts, but big journeys always start with small steps. When it comes to physical locations, we recommend you look into:
• Server rooms, the heart of your business data. Establishing a faraday setup is one such safety strategy, providing an incredibly secure ‘cage’ for your data, but bunkering it in also limits how easily your own employees and systems can access that information as part of your normal business practices.
• EM/RF shielding glass is another protective option and one that can be far more flexible in how it secures your sensitive data. It can be tailored to your unique security policies and settings, offering a fully transparent protective layer. It’s not impact proof, but it can be combined with other glass properties (such as fire-resistant and anti-burglary materials)
Why not involve your architect, contractor, office facilities manager to look into the matter and ask them which preventative measures might contribute to a bigger (cyber)security scope?
How can companies avoid vulnerabilities from a structural perspective?
Adopting a holistic approach will be crucial. The entire workforce will need to keep the helicopter overview while enforcing a very practical can-do mindset. The only way to hold everyone accountable is by following pointers like these:
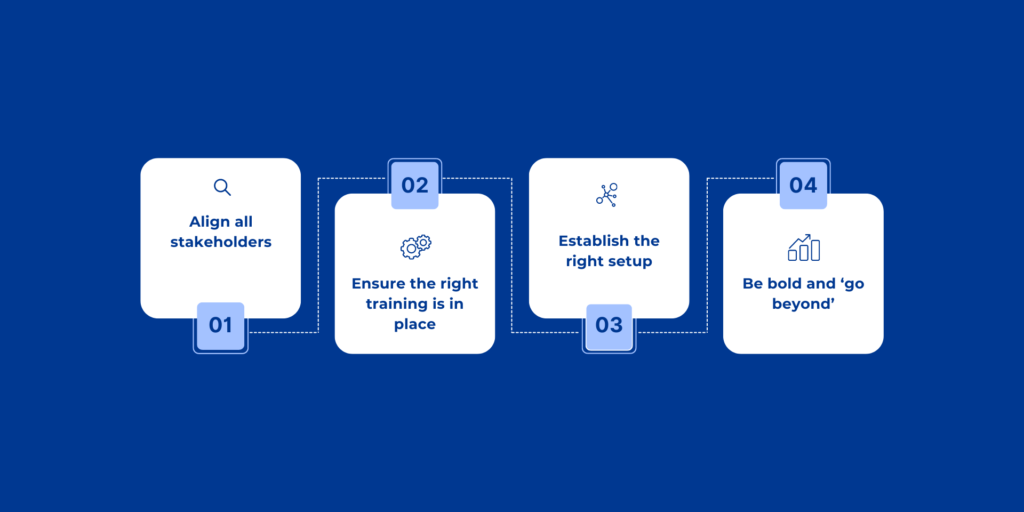
1. Align all stakeholders
All stakeholders in the business need to be aligned and on the same page when it comes to addressing security concerns and how this brings the company into compliance with NIS2. This includes C-level management and IT managers but also project managers, architects, contractors and more.
2. Ensure the right training is in place
All these new security measures might make sense to you or the team that’s procured and implemented them, but that won’t come into their own unless all members of staff in the workplace (both on-site and remote) have completed the relevant training to ensure these updated IT and security policies are understood.
3. Establish the right setup
Unsurprisingly, having the right settings in place to apply these best practices is a must. Be proactive and install both physical and virtual firewalls to protect your data at both levels. A technology such as EM/RF shielding glass is ESI-compliant, making it an ideal solution for businesses looking for a tailored glazing solution.
4. Be bold and ‘go beyond’
Never, ever settle, just because a potential solution seems easier or more cost effective. As cliche as it may sound, you simply cannot put a price on the integrity of your business data. Hackers are constantly evolving their means of attack, so you can’t afford to rest on your laurels. Minimise the risk by maximising your security options.
Conclusion
There’s unlikely to ever be a watertight solution that fixes every cybersecurity issue or woe, but that doesn’t mean you can’t take steps to ensure you’re NIS2 compliant. As with any ISO standardisation method out there, ensuring you’re fully compliant is the safest bet.
With WAVETRAP EM/EF shielding glass, you can leverage a fully ESI-compliant solution that’s been trialed, tested, and validated by the KU Leuven.
If you would like to learn more about NIS2-compliant security measures, such as EM/RF shielding glass, contact one of our experts today.

